A solid cyber defense strategy can protect plant assets—even field devices and pumps—from dangerous and costly security breaches.
03/11/2015
A plant's industrial control system (ICS) is no longer an island, and a field device—once ranked low in the risk and threat analysis table—is no longer safe simply because it is protected by its own control configuration. Today, a cyberattack can be initiated at any point in a plant's interconnected industrial system. For this reason, plant managers must consider cybersecurity at every level of the plant—from the business network to each critical field device and pump. Failure to do so could have catastrophic effects on both human safety and production.
System Complexity
Industrial systems consist of an array of devices, systems and software that are used to control, monitor and report vital data, making them a prime target for malicious activity. Reports of rogue databases, such as Shodan, show that these programs can openly report devices and systems connected to the Internet. They reveal critical system information—including location, purpose and protocol—that a hacker can use to compromise a system, cause damage and interrupt production. The advent of wireless connectivity and the Internet of Things presents a totally new threat vector that puts even field devices at risk. While much of the modern wireless technology available today (including tools that are compliant with WirelessHART and ISA100) is fairly secure, wireless devices and programs can suffer interference from any Wi-Fi, Bluetooth or other wireless device operating in the same frequency band. Even wireless printers and scanners pose a threat, because most wireless printers come with the wireless facility switched on by default, which alone could compromise an ICS.
The Standards
Despite the countless variables at play, plants can employ an effective approach: Adopt an information security management system, as defined by the International Standards Organization (ISO27001), and comply with standards put forth by the International Society of Automation (ISA99) and the International Electrotechnical Commission (IEC62443). ISO27001 was designed as a methodology to address security. It lists a number of controls companies can use to employ policies and procedures that address system confidentiality, integrity and availability.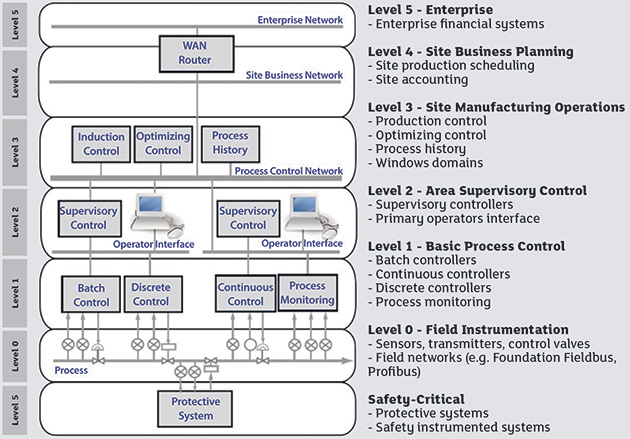 Figure 1. This diagram shows a comprehensive cybersecurity standard set. One of the most important things a company can do to prevent cyberattack is to follow best practices recommended by established standards bodies. ISA-62443 is one of the most comprehensive standards and eventually could encompass all of the others. Diagram shows planned and published standards.
(Graphics courtesy of Schneider Electric. Source ISA-99 Standards Committee)
Figure 1. This diagram shows a comprehensive cybersecurity standard set. One of the most important things a company can do to prevent cyberattack is to follow best practices recommended by established standards bodies. ISA-62443 is one of the most comprehensive standards and eventually could encompass all of the others. Diagram shows planned and published standards.
(Graphics courtesy of Schneider Electric. Source ISA-99 Standards Committee)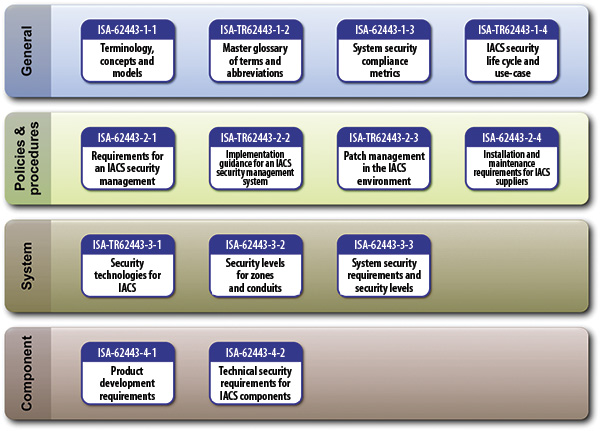 Figure 2. This chart depicts enterprise cyber protection layers. A cybersecurity assessment begins with an identification of the areas that need to be protected. The ISA-99 standard recommends six levels.
(Source: ISA-99 Standards committee)
Figure 2. This chart depicts enterprise cyber protection layers. A cybersecurity assessment begins with an identification of the areas that need to be protected. The ISA-99 standard recommends six levels.
(Source: ISA-99 Standards committee)The Strategy
The first step is to assess the risks and threats that might be associated with each layer. To do this, managers must consider their plants' target levels and evaluate the consequences of a cyberattack for each level. What are the chances of this level being exploited and by whom? What skillset and knowledge would be required to compromise this element? Would a compromise at this level result in loss of life or production? The results of this assessment reveal what type of access or knowledge is needed to compromise each level and indicate the most critical areas that need protection. Addressing ICS security by implementing safeguards in this way is known as creating layers of defense. No one exercise or handbook can dictate what security is needed for each layer in a particular company. Layers are defined by the security gaps within an organization. Finding these holes requires a site-specific gap analysis that identifies a company's current situation and the factors that are preventing it from achieving maximum security. To identify existing security gaps, analyze each level and the communications to the next level. The standards ISA99 and IEC62443 refer to this process as identification of zones and conduits. For example, if a plant started at Level 0 designating all of their pumps in a zone, the conduit would be the communication between the pump and the next device in line (see Figure 3). Figure 3. Example of communication between devices
Figure 3. Example of communication between devices
Read more about this topic here.
10 Steps to a Fortified Cyber Defense System
- Assess vulnerabilities of inventory-critical assets.
- Implement plans and systems to eliminate vulnerabilities.
- Manage electronic access to controls using physical or logical network segmentation.
- Manage user access to controls through user privilege and password management.
- Keep operating system and software patches up-to-date.
- Enable advanced antivirus software, and keep it current.
- Back up software regularly, and create an incident-response plan.
- Establish and enforce rigid policies for using flash drives, CD-ROMs and the Internet.
- Seek vendor assurance that servers, workstations and other systems are hardened and standards-compliant.
- Stay current on industry standards such as ISA99, IEC62443, ISA Secure, WIB and IEC62443, and review operations accordingly.

